Last Wednesday, security researcher, Stéphane Chazelas discovered a security vulnerability in the command line shell, GNU Bourne Again Shell—more commonly known as Bash. The bug, dubbed Shellshock, appears to be affecting Unix-based operating systems, including Linux and Mac OS X, as well as webservers running any version of Bash. Every version of Bash’s 25 year-old life span, including version 4.3, appears to be vulnerable.
Kasper Lindegaard, the head vulnerability intelligence specialist at the security firm Secunia, believes Shellshock could be “‘worse than Heartbleed,’ the open source flaw that left passwords vulnerable to hackers,” because “Bash enables hackers to execute commands to take over your servers and systems.”
Shellshock is allowing even the most inexperienced hackers to hijack vulnerable computers with just a few lines of code. Cyber security experts have warned that hackers could infect thousands of machines with malware to make them responsive to hackers’ arbitrary commands.
Security researcher, Robert David Graham wrote a proof-of-concept script to measure the extent of the problem. The code was meant to inform Graham of the infected computers, however, the hackers behind the exploit rewrote his code. This allowed them to install “malware that gave them a backdoor to victims’ machines.” These are courteous hackers though, as they left Graham a comment in the exploit code that read, “Thanks-Rob.”
According to Wired, researchers at the Russian antivirus firm, Kaspersky Lab, attempted to “examine the malware, locate its command and control server and intercept the DDoS commands it’s sending, but haven’t determined how many computers have already been infected.” Many in the cyber security community fear that the bug could evolve into a “worm,” which would increase the number of infected machines exponentially.
Roel Schouwenberg of Kaspersky explained that the only thing keeping hackers from turning Shellshock into a worm is, “the spread becomes uncontrollable. It generally makes more sense to ration this thing out rather than use it to melt the internet.”
But the urgency of the Bash bug made the government cyber security team respond quickly. Shortly after the announcement, the United States Computer Emergency Readiness Team (CERT) released a GNU Bash Patch for system administrators. Red Hat released a patch for Linux users as well, but announced that the patch is incomplete. The CERT provided Mac users with a simple command line of code that will allow them to test the vulnerability of their system.
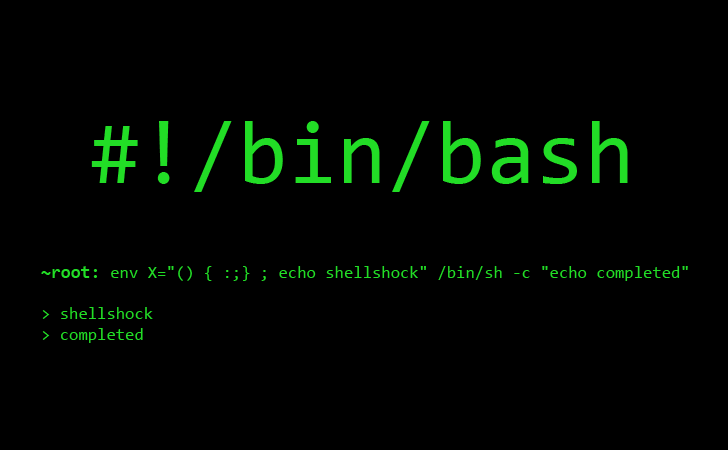
Users can enter the following command:
env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
If the system is vulnerable, the output will be:
vulnerable
this is a test
An unaffected (or patched) systems will output:
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x’
this is a test
Apple spokesperson, Bill Evans, said, “With OS X, systems are safe by default and not exposed to remote exploits of bash unless users configure advanced UNIX services. We are working to quickly provide a software update for our advanced UNIX users.” Apple has not identified the potentially problematic “advanced” UNIX services.
The severity of Shellshock on the cyber world remains unknown. Chief technology officer at security firm BeyondTrust, Marc Maiffret said, “There is a lot of speculation out there as to what is vulnerable, but we just don’t have the answers. This is going to unfold over the coming weeks and months.”
